For the second year in a row, the State of Open Source Report included a section on security tooling, and this year, we also added a few questions about open source compliance, to better understand how the regulatory landscape is evolving. The findings reveal both progress and persistent challenges that demand attention — for IT leaders, understanding these trends is essential for making informed decisions about risk management and resource allocation.
Keep reading to see which open source security tools are the most frequently implemented, how organizations prioritize different proactive security measures, and how many failed compliance audits last year.
Top Open Source Security Tools
When asked which open source security tools are being used in their organization, almost a third (32%) of respondents said “Our security tools are not open source”— which was the most popular answer to the question. This suggests that either awareness of available open source security tools is lacking or many organizations are deliberately choosing proprietary solutions over open source alternatives.
If the latter, it could be the case that some organizations have a trust issue with open source security solutions. Either way, teams may be missing opportunities to leverage cost-effective, open source security tools that could enhance their overall security posture.
Despite the abundance of open source security solutions available, as mentioned above, adoption rates remain surprisingly low. Out of 24 open source security technologies on the survey, only four were selected by more than 10% of respondents:
- Nmap (21.39%): Network discovery and security auditing — also the top tool in the previous year’s survey
- Dependabot (14.45%): Automated dependency updates
- OWASP Dependency-Track (12.72%): Component analysis platform
- Metasploit (10.40%): Penetration testing framework
The other 20 technologies with single-digit usage included firewalls like pfSense, SBOM generators like Syft and CycloneDX-CLI, vulnerability scanners like Trivy and Vuls, and threat detection tools like Suricata and OSSEC.
Back to topSecurity Practices and Priorities
According to the report, 59% of organizations actively scan their OSS for vulnerabilities — a slight uptick from last year (55%). This is a positive indicator that most IT teams recognize the importance of taking a proactive approach to security. However, this also means that 41% are operating without regular vulnerability scanning, exposing themselves to significant risk.
A few ways to make sense of this data: Generally, organizations with more mature OSS governance policies are more likely to perform security scans. And while scanning itself is not generally expensive or difficult, resolving issues flagged by scanning absolutely can be, as it often means updating dependencies, performing QA, and, in some cases, application changes to address changes introduced by those updates. Since these efforts are unpredictable in nature, they can derail work on application features. As a result, some teams likely are struggling to balance technical debt and security with delivering business value.
We also asked respondents to rate from 1 to 5 a number of proactive security measures. Here are the weighted averages:
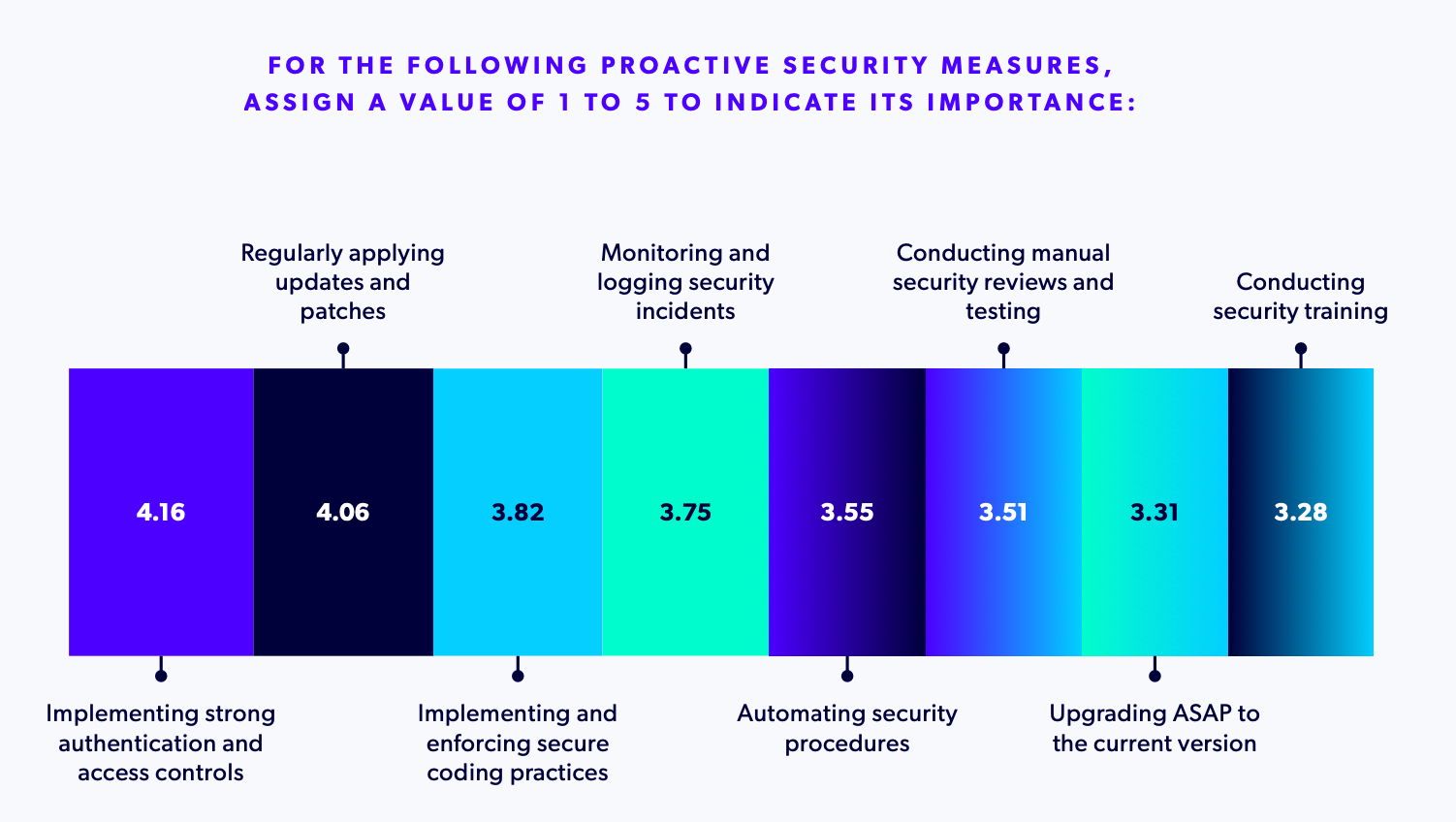
Engineers are often characterized as being enticed by "the new shiny", and quick to adopt new technologies and new versions of software they use. These numbers show that this is not necessarily the case — in fact, they detail that when it comes to security, they are more likely to adopt bugfix and security fix releases than new feature releases. This is overall a good thing, as it means that their focus is on security and delivering business value, and less on being on the cutting edge — where security often hasn't been fully tested.
On the flip side, less value is placed on security training, which is problematic. When there is too much confidence in security, engineers may miss developing trends in the security ecosystem that could negatively impact their applications.
Breaking out the data by company size, it’s also clear that size influences security strategies. For example, monitoring and logging security incidents and implementing and enforcing secure coding practices are a higher priority for organizations with fewer than 500 employees. This could be because larger enterprises have already established these foundational practices and are focusing on more advanced security initiatives.
Back to topGet Ahead With Insights From the State of Open Source Report
Find out what's driving OSS adoption, which technologies are being used in mission-critical apps, how teams are approaching security and compliance, and more! Based on a global survey of open source users working in 20+ industries.
Open Source Compliance Challenges
The compliance landscape has become increasingly complex, with 84% of organizations required to meet internal and/or external compliance policies.
Take a look at this graph from the report:
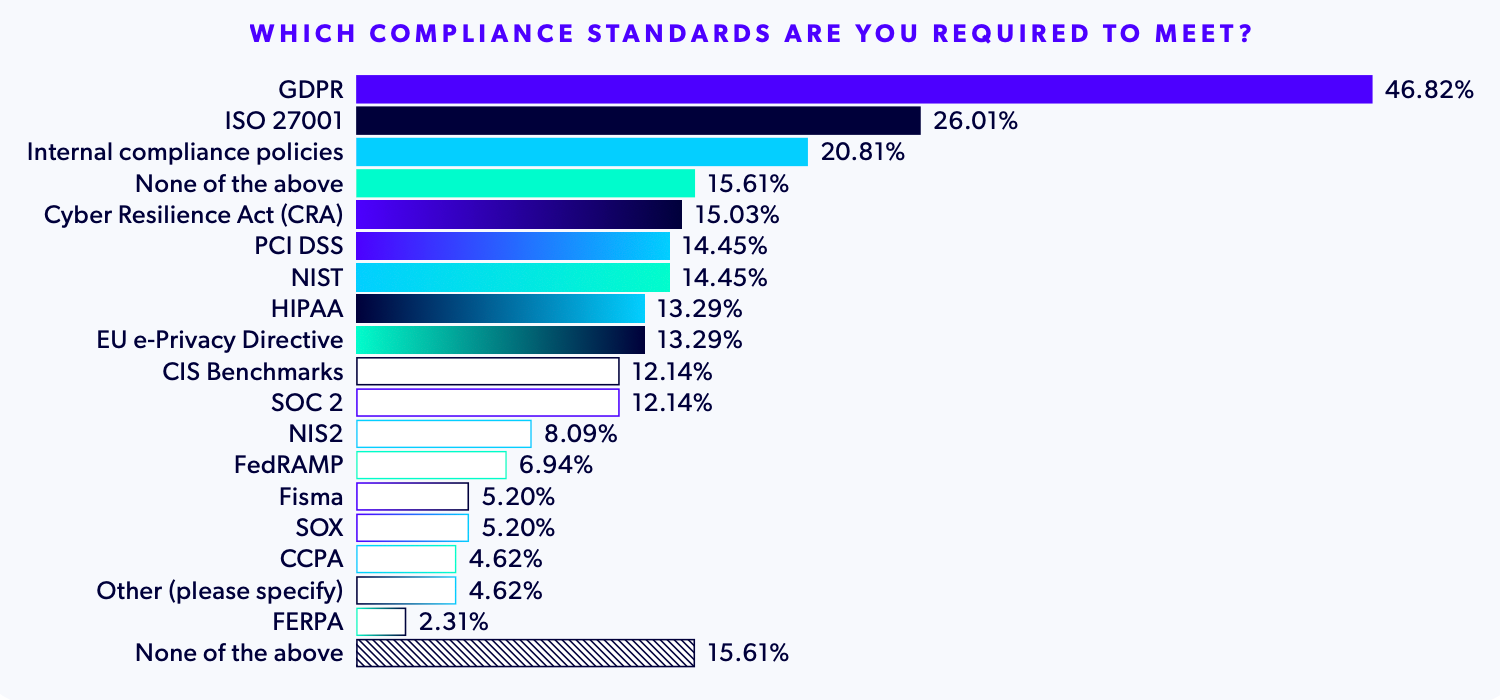
The above chart demonstrates that compliance is no longer optional for most enterprises — it's a fundamental business requirement that directly impacts operational capabilities.
The variety of regulatory requirements creates additional complexity:
- Regional regulations such as GDPR, CRA, and EU e-Privacy Directive affect those operating or doing business in European countries
- Region and sector-specific regulations like FedRAMP for U.S. federal agencies and DORA for financial services providers operating or doing business with the EU
- Sensitive data-related regulations like HIPAA for healthcare data, FERPA for educational records, and PCI DSS for credit card information
Watch the Webinar: The State of Open Source in 2025
Experts from Perforce Software, the Open Source Initiative, and the Eclipse Foundation discuss the key takeaways for IT leaders in this year's State of Open Source Report.
Who Is Failing Compliance Audits?
Only 14% of our survey population said they failed a compliance audit in the past year, which seems like a manageable number. However, deeper analysis reveals some concerning patterns:
- Companies in Africa and Asia failed more compliance audits last year than companies in other parts of the world
- More than a quarter (28%) of the largest enterprises (with 5K+ employees) failed audits
- 21% of organizations in the most highly regulated sectors (finance, manufacturing, healthcare, energy, telecommunications) failed audits
These disparities suggest that compliance challenges are not distributed evenly across the global business landscape. Specifically, larger organizations in certain regions and industries may need to direct more attention and resources to maintain compliance.
End-of-Life Software Creates Compliance Risks
The connection between outdated software and compliance failures is stark. 41% of organizations using end-of-life software (such as CentOS and AngularJS) failed audits last year. Put another way, running EOL software nearly triples the risk of failing a compliance audit.
This correlation demonstrates the importance of moving off of legacy systems and regularly performing updates in order to stay on current, or at least not deprecated, versions. It also underscores the need for robust software lifecycle management processes and long-term support in cases where it’s not possible to migrate immediately off of EOL OSS.
Back to topNeed Long-Term Support or Migration Services?
Protect your EOL open source software with LTS from OpenLogic. We can also help you plan and execute your migration to a supported technology. Click the buttons below to learn more.
Final Thoughts
The State of Open Source Report security and compliance findings can be summarized into three key insights:
- Open source security tools are worth exploring — especially if you’re in the 41% not scanning your OSS for vulnerabilities!
- Compliance readiness must be proactive. It’s essential to know which regulations apply to your organization and how to comply with them, whether that’s being able to patch EOL software, harden your Linux servers according to CIS Benchmarks, secure your data infrastructure, or something else.
- Software lifecycle management directly impacts compliance success. Migrate off of legacy systems and get LTS to bridge the gap while you plan your migration. This is particularly essential if you are subject to the new DORA compliance regulations in the EU.
More on the State of Open Source Report
- Highlights from the 2025 State of Open Source Report
- The State of Enterprise Linux Distributions After CentOS EOL
- Top Open Source Databases and Big Data Technologies of 2025
- Archive of Previous Reports
Additional Security Resources
- Blog - Applying CIS Benchmarks to Your Linux OS With Hardened Images
- Webinar - Why Open Source Compliance Matters
- Video - Risks of Ignoring EOL Software
- Video - Open Source Software Compliance
- Blog - Best Practices for Web Server Security
- Blog - Understanding CVEs and CVSS Scores
- Blog - Debunking Open Source Software Security Myths
- Blog - Navigating Software Dependencies and OSS Inventory Management