Technical Support & Professional Services for Your Open Source Infrastructure
Supporting open source software in-house can be an ongoing obstacle to innovation — and ultimately impact your business goals. OpenLogic by Perforce provides the expert technical support needed to succeed with open source, giving your teams the freedom to focus on driving your business forward.
With SLA-backed technical support for over 400 open source packages, and direct access to experienced enterprise architects, OpenLogic customers receive comprehensive technical support and professional services built for the enterprise — all in one place.
Guaranteed SLAs
24/7/365 Support Delivered by Enterprise Architects
Enterprise Support for 400+ Open Source Packages
Open Source Migration Services and Consultative Guidance
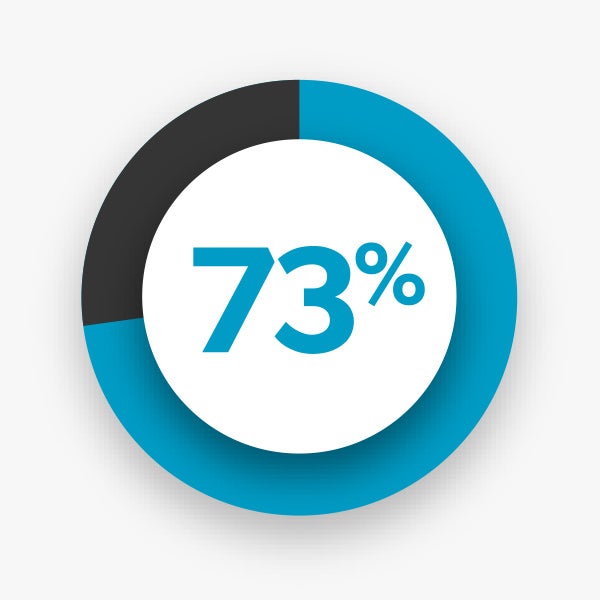
73% of recipients stated the need for external support and services to achieve open source success.
Why Choose OpenLogic?
OpenLogic acts as your trusted advisor, helping you reach OSS maturity and achieve business goals.
What Our Customers Are Saying
“Support with OpenLogic allowed us to drive an internal repository to centrally manage CentOS versions easily and deploy them rapidly.”

OpenLogic enabled us to avoid downtime, reduce organizational costs, maintain security compliance, and facilitate an overall source risk strategy.

OpenLogic’s end of life / long term support maintenance capabilities are crucial to our Linux deployments.

“Compared to other vendors they have previously evaluated or used, Kronos Incorporated rated OpenLogic’s Ticket Response Time as best in class.”
82% of surveyed organizations rated OpenLogic’s range of packages supported as superior compared to other vendors they have previously evaluated or used.
“With OpenLogic we are able to use OSS with Enterprise Class Support.”
“OpenLogic has provided an alternative solution to high cost commercial licensed products, that allow our customers to stand up an environment quicker, and at lower cost.”
82% of surveyed organizations confirmed that OpenLogic enabled them to reduce maintenance.
Explore Our Core Packages
Extend the Life of EOL CentOS
As of June 2024, CentOS 6, 7, and 8 will all be end-of-life. OpenLogic has experts who can advise you about next steps while providing long-term support that includes patches for high severity vulnerabilities.
Save Money With AngularJS
OpenLogic provides LTS for EOL AngularJS, including security patches for medium and high severity CVEs and fixes for web browser or jQuery updates that cause breaking changes.
Master Your Open Source Middleware
Ensure your open source message-oriented middleware is ready for prime time with security, performance, and scalability optimization from our open source experts.