
Need More VPN Capacity? Try OpenVPN with PFSense!
During the COVID-19 pandemic, many companies have struggled to sustain secure VPN capacity. In this blog, we look at the current state of VPNs, and methods for expanding and optimizing your current VPN capacity without increased licensing costs.
The Current State of VPNs
Before the global COVID-19 crisis, many businesses had intermittent usage of Road Warrior VPN, which allows users anywhere in the world, or certain geographies, to connect to the corporate LAN and access internal resources. Only some users were enabled, and those users were only road warriors some for the time during the work week (or weekend).
Companies are much more likely to be invested in site-to-site VPNs, which connect remote offices securely through technologies like IPSEC. IPSEC, though, can be complicated and insecure to set up for road-warrior users, might not be able to utilize technologies like Perfect Forward Secrecy (PFS) with their operating system provided VPN clients.
Increasing VPN Capacity With PFSense
Many companies facing the COVID-19 crisis are struggling to keep up with VPN capacity, and in a secure way. If your existing VPN appliance is struggling to keep up with the number of connections, which are CPU intensive (all that encryption!), consider utilizing some of your site-to-site capacity, and fanning out your VPN users to the cloud, and connecting those cloud nodes over IPSEC tunnels to your corporate VPN, like this!
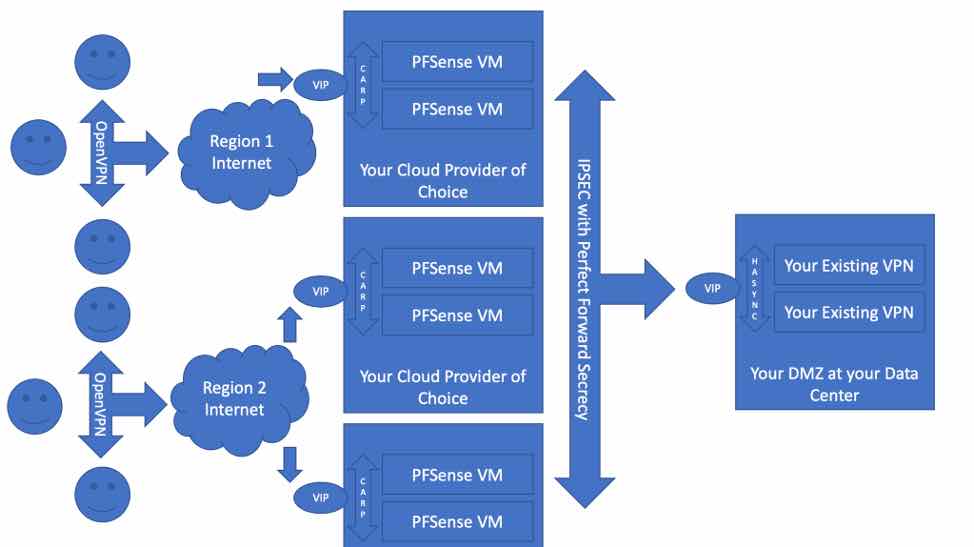
This avoids the high cost of unanticipated volume of VPN users, reduces the load on the existing VPN appliances, and scales down when the crisis is over without long-term contracts. We can accomplish this configuration with an easy, GUI-based software appliance called PFSense, which can auto-generate OpenVPN configurations and binaries, and can even authenticate against your users against existing Active Directory Domain Controllers!
Why Is This Superior to Direct-to-LAN, Road Warrior VPN?
Many businesses without a robust road warrior strategy already in may be struggling to accomplish policies that secure the business against external threats, while allowing the right employees access to the appropriate environments. By utilizing a cloud-based strategy, companies can bolt-on CPU-intensive strategies like using Snort for Intrusion Detection, On-Access Anti-Virus through ClamAV, and other similiarly CPU-bound strategies that scale beautifully on the cloud.
With these technologies, all integrated seamlessly into PFSense, companies can detect and mitigate fairly advanced threats like virus payloads and malicious traffic that might otherwise overload an already taxed remote work infrastructure. And when the remote workers return to the office? Spin down the remote cloud.
What Is PFSense?
PFSense is an open source firewall and router software based on FreeBSD, and exists as a fork of the m0n0wall project.
Some of you oldschool OSS users might remember it as a great project to use for captive portal installations, for example, guest WiFi at hotels. But the PFSense community has come a long way to creating a great OSS router and firewall computer software distribution based on FreeBSD. It has an intuitive wizard-based web interface and requires no knowledge of the underlying FreeBSD system to manage.
Final Thoughts
If you’re interested in expanding your existing VPN capacity without increasing licensing costs, or upgrading your VPN appliances, (without having to send multiple employees into datacenters and putting them at risk) OpenLogic by Perforce can help you set up a fan-out VPN environment remotely.
This project can be completed quickly, and we can get your newly remote employees back on track and up to speed. Let us know if we can help!
